In the vast landscape of network communications and data transmission, you may have encountered the term source address 5910d068. This unique identifier plays a crucial role in various aspects of digital communication, from troubleshooting network issues to ensuring secure data transfer.
In this comprehensive guide, we'll delve deep into the world of source addresses, with a particular focus on source address 5910d068, its significance, and its applications in modern networking.
What is source address 5910d068?
Source address 5910d068 is a unique identifier used in network communications to pinpoint the origin of data packets or network traffic. This hexadecimal address plays a crucial role in various networking scenarios, from troubleshooting to security analysis.
While the exact nature of source address 5910d068 may vary depending on the context, it generally serves as a digital fingerprint for a specific device, interface, or communication channel within a network infrastructure.
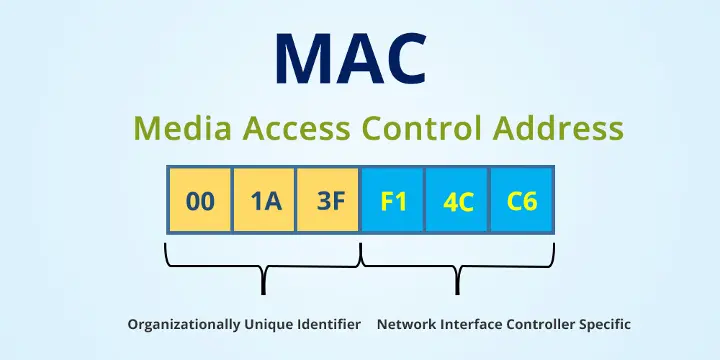
Decoding Source Address 5910d068
Now, let's focus on our specific example: source address 5910d068. This particular address is a hexadecimal representation, which is common in various computing and networking contexts. Let's break it down:
- "5910" - The first part of the address
- "d068" - The second part of the address
While the exact meaning of source address 5910d068 may vary depending on the context, it's likely associated with a specific device, network interface, or communication channel.
Common Uses of Source Address 5910d068
Source address 5910d068 could be utilized in several scenarios:
- Network Troubleshooting: Network administrators might use source address 5910d068 to identify the origin of network traffic, helping diagnose connectivity issues or unusual network behavior.
- Security Analysis: In cybersecurity, source address 5910d068 could be monitored to detect potential threats or unauthorized access attempts.
- Data Routing: Routers and switches might use source address 5910d068 to determine the best path for data packets to reach their destination.
- Device Identification: In some systems, source address 5910d068 could be associated with a specific hardware device or network interface card.
- Communication Protocols: Certain protocols might use source address 5910d068 as part of their addressing scheme to ensure proper data transmission.
The Importance of Source Addresses in Networking
Understanding source addresses like 5910d068 is crucial for several reasons:
1. Network Performance Optimization
By analyzing traffic patterns associated with source address 5910d068, network administrators can optimize network performance. This might involve:
- Load balancing
- Traffic shaping
- Quality of Service (QoS) configurations
2. Security Enhancement
Source address 5910d068 can play a vital role in network security:
- Identifying potential security threats
- Implementing access control lists (ACLs)
- Detecting and preventing IP spoofing attacks
3. Troubleshooting and Diagnostics
When network issues arise, source address 5910d068 can be a valuable piece of information for:
- Tracing the origin of problematic traffic
- Identifying misconfigured devices
- Resolving connectivity problems
4. Compliance and Auditing
In some industries, tracking and logging source addresses like 5910d068 is necessary for:
- Regulatory compliance
- Network auditing
- Forensic analysis
Technical Aspects of Source Address 5910d068
Let's delve deeper into the technical aspects of source address 5910d068:
Hexadecimal Representation
The address "5910d068" is in hexadecimal format, which is base-16. This means it uses 16 distinct symbols: 0-9 and A-F. Hexadecimal is commonly used in computing because it can represent binary data more concisely than decimal notation.
Possible Interpretations
Depending on the context, source address 5910d068 could represent:
- IPv6 Address Segment: It might be part of a larger IPv6 address, which uses 128-bit addresses typically represented in hexadecimal.
- MAC Address Component: It could be a portion of a MAC address, which identifies network interface cards at the data link layer.
- Memory Address: In some systems, it might represent a memory address where specific data or instructions are stored.
- Custom Protocol Identifier: Some proprietary or specialized protocols might use source address 5910d068 as a unique identifier within their system.
Practical Applications of Source Address 5910d068
Understanding and utilizing source address 5910d068 can have several practical applications:
1. Network Monitoring and Analysis
Network administrators can use tools to monitor traffic associated with source address 5910d068. This can help in:
- Identifying unusual traffic patterns
- Monitoring bandwidth usage
- Detecting potential network bottlenecks
2. Firewall Configuration
Firewalls can be configured to allow or block traffic based on source addresses. For example:
if source_address == "5910d068": allow_traffic() else: block_traffic()
This simple pseudocode demonstrates how a firewall might use source address 5910d068 in its decision-making process.
3. Intrusion Detection Systems (IDS)
An IDS might flag traffic from source address 5910d068 if it matches certain criteria:
- Unusual port access attempts
- High-frequency connection requests
- Known malicious behavior patterns
4. Network Address Translation (NAT)
In NAT configurations, source address 5910d068 might be translated to a different address for external communications:
Original source: 5910d068 Translated source: 203.0.113.45
This process helps in preserving IP addresses and enhancing network security.
Challenges and Considerations
While source address 5910d068 can be a valuable piece of information, there are some challenges and considerations to keep in mind:
1. Address Spoofing
Malicious actors might attempt to spoof source address 5910d068 to:
- Bypass security measures
- Hide their true identity
- Launch Denial of Service (DoS) attacks
2. Dynamic Addressing
In networks using dynamic addressing, source address 5910d068 might not always be associated with the same device or interface. This can complicate long-term monitoring and analysis.
3. Privacy Concerns
Tracking and storing data associated with source address 5910d068 might raise privacy concerns, especially if it can be linked to individual users or sensitive information.
4. Compatibility Issues
Not all networking equipment or software may be capable of properly handling or interpreting source address 5910d068, particularly if it's part of a newer or specialized protocol.
Best Practices for Handling Source Address 5910d068
To effectively work with source address 5910d068, consider the following best practices:
- Regular Monitoring: Implement systems to regularly monitor and log traffic associated with source address 5910d068.
- Security Measures: Use firewalls, intrusion detection systems, and other security tools to protect against potential threats associated with this address.
- Documentation: Maintain clear documentation on the role and significance of source address 5910d068 within your network infrastructure.
- Update and Patch: Keep all systems and software up-to-date to ensure proper handling of source addresses and related network traffic.
- Employee Training: Educate relevant staff members on the importance of source addresses and how to properly interpret and handle source address 5910d068.
Future Trends and Developments
As networking technologies continue to evolve, the role and significance of source addresses like 5910d068 may change. Some potential future developments include:
- IPv6 Adoption: With the increased adoption of IPv6, we may see changes in how source addresses are structured and utilized.
- AI and Machine Learning: Advanced algorithms might be employed to analyze patterns and behaviors associated with source address 5910d068 more efficiently.
- Blockchain Integration: Blockchain technology could be used to create more secure and verifiable systems for managing and tracking source addresses.
- Quantum Networking: As quantum computing and networking technologies develop, we may see entirely new paradigms for addressing and routing.
Conclusion
Source address 5910d068 is more than just a string of characters—it's a crucial component in the complex world of modern networking. Whether you're a network administrator, cybersecurity professional, or simply someone interested in the intricacies of digital communication, understanding the role and significance of source addresses is invaluable.
By leveraging the information and best practices discussed in this guide, you can better navigate the challenges and opportunities presented by source address 5910d068 and similar network identifiers. As technology continues to advance, staying informed and adaptable will be key to maintaining efficient, secure, and robust network infrastructures.
Remember, while source address 5910d068 may seem like a small detail in the grand scheme of networking, it's these precise identifiers that form the backbone of our interconnected digital world. By paying attention to these details, we can build more resilient, efficient, and secure networks for the future.
Source Address 5910d068: A Comprehensive Guide